Better place for software
03.06.2015., srijeda
Malwarebytes Anti-Exploit v1.06 2015
|
Stop being exploited Popular software programs contain millions of lines of code. Bad guys exploit flaws (vulnerabilities) in the code to deliver malware. Except when they can't. Malwarebytes Anti-Exploit wraps four layers of security around popular browsers, preventing exploits from compromising vulnerable code. Not an antivirus, but compatible with most antivirus, Malwarebytes Anti-Exploit is a small, specialized shield designed to protect you against one of the most dangerous forms of malware attacks. And it's free. Tech Specs Version: 1.06 Click Here to view our full product release history. Operating Systems: Windows 8.1® (32-bit, 64-bit) Windows 8® (32-bit, 64-bit) Windows 7® (32-bit, 64-bit) Windows Vista® (32-bit, 64-bit) Windows XP® (32-bit, 64-bit) Hardware Requirements: 1024MB of RAM (256MB for Windows XP) 800MHz CPU or faster 10MB of free hard disk space 800x600 or greater screen resolution Download |
- 17:50 - Komentari (0) - Isprintaj - #
RogueKiller 10.8.1.0
|
RogueKiller is an anti-malware program written in C++ and able to detect and remove malwares and some advanced threats such as rootkits, rogues, worms,etc Based on ways to find malware by their behaviour (heuristics), on classic anti-malware analysis (signature finding) and on undocumented hacks, RogueKiller can find/remove most of the basic malware (rogues, trojans, …) and some advanced threats like ZeroAccess or TDSS that behave more like rootkits. RogueKiller is an anti-malware maintained by a small team, and thus new detections are based on “most spread threats“. We react quickly to integrate detection and removal of what we think can be a global threat and affect a big amount of users across the world. Here’s a little summary of what RogueKiller is able to do: Kill malicious processes Stop malicious services Unload malicious DLLs from processes Find/Kill malicious hidden processes Find and remove malicious autostart entries, including : Registry keys (RUN/RUNONCE, …) Tasks Scheduler (1.0/2.0) Startup folders Find and remove registry hijacks, including : Shell / Load entries Extension association hijacks DLL hijacks Many, many others … Read / Fix DNS Hijacks Read / Fix Proxy Hijacks Read / Fix Hosts Hijacks Read / Fix malicious Master Boot Record (MBR) or Volume Boot Record (VBR), even hidden with a rootkit List / Fix SSDT – Shadow SSDT – IRP Hooks (Even with inline hooks) Find and restore system files patched / hidden by a rootkit New in RogueKiller 10.8.1.0: V10.8.1 06/03/2015 ================= - Fixed a bug in Licensing - Fixed a bug in VirusTotal module - Now portable license generated file is read-only - Added GUI indicators when using portable license - Added detections - Extension checker optimizations HOMEPAGE WINDOWS ALL 32Bit Portable 64Bit Portable |
- 17:38 - Komentari (0) - Isprintaj - #
I2P: The Super-Anonymous Network
|
The Invisible Internet Project (I2P)is an anonymous network, exposing a simple layer that applications can use to anonymously and securely send messages to each other. The network itself is strictly message based (a la IP), but there is a library available to allow reliable streaming communication on top of it (a la TCP). All communication is end to end encrypted (in total there are four layers of encryption used when sending a message), and even the end points ("destinations") are cryptographic identifiers (essentially a pair of public keys). How does it work? To anonymize the messages sent, each client application has their I2P "router" build a few inbound and outbound "tunnels" - a sequence of peers that pass messages in one direction (to and from the client, respectively). In turn, when a client wants to send a message to another client, the client passes that message out one of their outbound tunnels targeting one of the other client's inbound tunnels, eventually reaching the destination. Every participant in the network chooses the length of these tunnels, and in doing so, makes a tradeoff between anonymity, latency, and throughput according to their own needs. The result is that the number of peers relaying each end to end message is the absolute minimum necessary to meet both the sender's and the receiver's threat model. The first time a client wants to contact another client, they make a query against the fully distributed "network database" - a custom structured distributed hash table (DHT) based off the Kademlia algorithm. This is done to find the other client's inbound tunnels efficiently, but subsequent messages between them usually includes that data so no further network database lookups are required. What can you do with it? Within the I2P network, applications are not restricted in how they can communicate - those that typically use UDP can make use of the base I2P functionality, and those that typically use TCP can use the TCP-like streaming library. We have a TCP/I2P bridge application ("I2PTunnel") that enables people to forward TCP streams into the I2P network as well as to receive streams out of the network and forward them towards a specific TCP/IP address. I2PTunnel is currently used to let people run their own anonymous website ("eepsite") by running a normal webserver and pointing an I2PTunnel 'server' at it, which people can access anonymously over I2P with a normal web browser by running an I2PTunnel HTTP proxy ("eepproxy"). In addition, we use the same technique to run an anonymous IRC network (where the IRC server is hosted anonymously, and standard IRC clients use an I2PTunnel to contact it). There are other application development efforts going on as well, such as one to build an optimized swarming file transfer application (a la BitTorrent), a distributed data store (a la Freenet / MNet), and a blogging system (a fully distributed LiveJournal), but those are not ready for use yet. I2P is not inherently an "outproxy" network - the client you send a message to is the cryptographic identifier, not some IP address, so the message must be addressed to someone running I2P. However, it is possible for that client to be an outproxy, allowing you to anonymously make use of their Internet connection. To demonstrate this, the "eepproxy" will accept normal non-I2P URLs (e.g. "http://www.i2p.net")and forward them to a specific destination that runs a squid HTTP proxy, allowing simple anonymous browsing of the normal web. Simple outproxies like that are not viable in the long run for several reasons (including the cost of running one as well as the anonymity and security issues they introduce), but in certain circumstances the technique could be appropriate. The I2P development team is an open group, welcome to all who are interested in getting involved, and all of the code is open source. The core I2P SDK and the current router implementation is done in Java (currently working with both sun and kaffe, gcj support planned for later), and there is a simple socket based API for accessing the network from other languages (with a C library available, and both Python and Perl in development). The network is actively being developed and has not yet reached the 1.0 release, but the current roadmap describes our schedule. Dependency Java Runtime 1.6 or higher. (Oracle, OpenJDK, or IcedTea Java Version 7 or 8 recommended, except Raspberry Pi: JDK 8 for ARM, PowerPC: IBM SDK 7) Determine your installed Java version here or type java -version at your command prompt. HOMEPAGE WINDOWS MAC |
- 15:49 - Komentari (0) - Isprintaj - #
01.06.2015., ponedjeljak
Windows Firewall Control 4.5.0.0
|
Microsoft Windows have already built-in default, free and powerful firewalls, but unfortunately, they lack a simple interface to define own simple rules and can be difficult sometimes to configure them the right way. Windows Firewall Control is a nifty little application which extends the functionality of the Windows Firewall and provides quick access to the most frequent options of Windows Firewall. It runs in the system tray and allows user to control the native firewall easily without having to waste time by navigating to the specific part of the firewall. Windows Firewall Control offers four filtering modes which can be switched with just a mouse click. WFC is free to use, registered users will get the advantage of learning mode which provides notifications for outgoing blocked connections. Changes in 4.5.0.0: New: Added a new button in the Rules Panel for columns configuration. When this button is clicked, it opens the same context menu as the right menu click from the data grid header. New: Added alternative ways to specify the color of the user interface in the Options tab, by using RGB values or by specifying the hex color. New: Invalid rules are automatically detected When opening the Rules Panel. They are displayed with red color and have a specific tooltip. Also, the color for temporary rules was changed to blue. New: Added a new warning message before opening for editing an inbound rule with EdgeTraversal set to 'Defer to user'. Editing of this kind of rule is not fully supported. New: Added the possibility to import, export or reset user settings. The new options were added under the Options tab in Main Panel. Improved: The text from several text boxes from Main Panel will be automatically selected when the controls will be focused to make it easier to quick pdate them. Improved: The URL services were moved from the Options tab to the Tools tab. Fixed: The default advanced notification settings are not the same when you make a clean installation and when you reset them to the default values. Homepage Changelog Download |
- 09:46 - Komentari (0) - Isprintaj - #
27.05.2015., srijeda
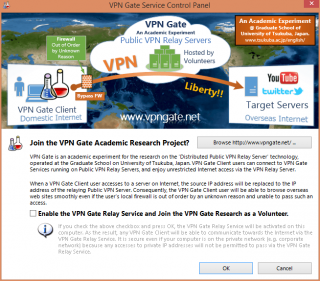
VPN Gate 2015
|
VPN Gate Academic Experiment Project is an online service as an academic research at Graduate School of University of Tsukuba, Japan. The purpose of this research is to expand the knowledge of "Global Distributed Public VPN Relay Servers" . Why VPN Gate? You can take these advantages by using VPN Gate: You can get through the government's firewall to browse restricted web sites (e.g. YouTube). You can disguise your IP address to hide your identity while surfing the Internet. You can protect yourself by utilizing its strong encryption while using public Wi-Fi. Unlike traditional VPN services, VPN Gate can get through most firewalls. VPN Gate is free of charge. Not a single registration is required. How does VPN Gate work? VPN Gate network consists of many VPN servers, which are provided by volunteers around the world. You can provide your own computer as a VPN server to join this experiment. Windows, Mac, iPhone, iPad and Android are supported. Supports ~ Phishing ~VPN (SoftEther VPN) protocol, L2TP/IPsec protocol, OpenVPN protocol and Microsoft SSTP protocol. Anonymous connections are accepted. No user registrations are required. Each VPN server has a dynamic IP address. Therefore it may change at random period. VPN servers appear and disappear at any time. Therefore, an IP address may not always connect to a VPN server. All VPN servers are capable of routing your traffic to the Internet, so you can disguise your real IP address. Using a server located somewhere other than your region may provide you some more accessible websites, because the comminucation would look as if it is originated from the country the VPN server resides. Simply install VPN Gate Client Plugin to SoftEther VPN Client. It will enable you to connect to any of our Public VPN Relay Servers of VPN Gate in a snap. It has a better throughput than L2TP, OpenVPN or SSTP. This program files are digitally signed by a certificate issued by GlobalSign. The binary file has a countersignature issued by Symantec. About Anti-Virus software This program uses the networking functions of the operating system for its core VPN capability. Some anti-virus software or firewalls warn that such behavior might be dangerous. If your anti-virus software disrupts the VPN function, add the VPN program file or the installer to its whitelist. Download | VPN Gate Client |
- 19:07 - Komentari (0) - Isprintaj - #
26.05.2015., utorak
Hamachi 2.2.0.328
|
LogMeIn Hamachi is a hosted VPN service that securely connects devices and networks, extending LAN-like network connectivity to mobile users, distributed teams and business applications. You can easily create secure virtual networks on-demand, across public and private networks. Hamachi is managed and maintained from anywhere via the web, securely. Homepage Changelog Download | 2.2.0.328 Final |
- 21:37 - Komentari (0) - Isprintaj - #
KeePass 2.29
|
KeePass is a free open source password manager, which helps you to manage your passwords in a secure way. You can put all your passwords in one database, which is locked with one master key or a key file. So you only have to remember one single master password or select the key file to unlock the whole database. The databases are encrypted using the best and most secure encryption algorithms currently known (AES and Twofish). Homepage Changelog Download Page Download | Installer Download | Portable Note: The listed version needs Microsoft .NET Framework 2.0 or newer. The Classic version available on the Download Page does not, but has less features. |
- 21:31 - Komentari (0) - Isprintaj - #
TinyWall 2.1.6
|
TinyWall has been designed to improve the default firewall of Windows. TinyWall lets you work while protecting you. There are no annoying popups but configuration is very simple. Using the advanced Windows Firewall built into newer Windows versions, TinyWall's performance impact is negligible. No drivers or kernel-components are installed so it does not influence system stability. Automatic learning, blocklists, password lock, firewall tampering protection and built-in tight firewall rules help increase TinyWall's and your computer's security even further. Firewall modes and lots of other convenience features make TinyWall extremely easy to use for anybody. All packed into a download that is about a megabyte. Changes in 2.1.6: Windows 10 (TP) compatibility Add color-coding to Application Exceptions list Faster loading of Manage and Processes windows Fix: GUI crashes when process list is cancelled Fix: Printer sharing doesn't create rule for spoolsv.exe Fix: Two rules can get incorrectly merged Fix: TinyWall loses its settings under specific circumstances Updated Brazilian Portuguese translation Add Chinese translation Homepage Changelog Release Notes Download |
- 19:47 - Komentari (0) - Isprintaj - #
Agnitum Outpost Security Suite Free 9.1
|
Outpost Security Suite Pro is a robust, proactive Internet security solution that protects against a broad range of current and future threats, from viruses and spyware to rootkits and botnets. What you get is: advanced firewall for secure connections, combined antivirus and antispyware for all-in-one malware defense, host protection to block zero-day threats, web control to protect your PC from web-borne threats, Antispam to automatically keep your inbox junk-free. Download | x86 Download | x64 |
- 19:01 - Komentari (0) - Isprintaj - #
Avast! 2015 10.2.2218
|
Avast! Pro Antivirus is for people and companies that want a customized computer security package. Antivirus and internet protection components in avast! Pro Antivirus are built for easy integration with existing firewalls in users' home or work computers. Pro Antivirus has two major additions to the core protection elements in avast! Free Antivirus: the Script Engine and the Sandbox. Download | 10.2.2218 Free |
- 18:50 - Komentari (0) - Isprintaj - #
Comodo Internet Security 8.2.0.4591
|
Comodo Internet Security offers 360° protection against internal and external threats by combining a powerful Antivirus protection, an enterprise class packet filtering firewall, and an advanced host intrusion prevention system called Defense+. Developed by one of the world's leading IT security providers, COMODO AntiVirus leverages multiple technologies(including on demand & on access scanning, email scanning, process monitoring and worm blocking) to immediately start protecting your PC. The new-look interface facilitates quick and easy access to all major settings, including the powerful and highly configurable security rules interface. Download | Premium Download | Firewall Only |
- 18:48 - Komentari (0) - Isprintaj - #
24.05.2015., nedjelja
Symantec Endpoint Protection 12.1.6168.6000 (x86/x64)
|
Symantec Endpoint Protection 12 brings unrivaled security and blazing performance across physical and virtual systems and is equipped to protect the latest operating systems achieving maximum performance and advanced protection. Symantec Insight technology reduces antivirus scans while SONAR stops cyber-criminals and zero-day attacks. Only Symantec Endpoint Protection 12 provides the security you need through a single, high-powered agent, for the fastest, most-effective protection available. New Features: Support for the latest operating system Effectively protects your Mac OS X 10.9 (Mavericks) and Windows 8.1. IPS & AV layered protection for Mac Provides unrivaled security with a single, high-powered agent that integrates both IPS and antivirus for Mac users. Fast Path feature Allows you to identify critical events almost in real-time to create the fastest, most effective solution available. Seamless console experience Eliminates confusion between Mac and Windows. Unrivaled Security. Blazing Performance. Built for Virtual Environments. Symantec Endpoint Protection is built on multiple layers of protection, including Symantec Insight and SONAR both of which provide protection against new and unknown threats. Built for virtual environments, it can integrate with VMware vShield Endpoint for dramatically improved performance. Symantec Endpoint Protection 12 includes the latest features for improved security, performance and management. Download | x86 Download | x64 Official Page |
- 13:55 - Komentari (0) - Isprintaj - #
23.05.2015., subota
Trojan Remover 6.9.2 Build 2938
|
Trojan Remover aids in the removal of Malware - Trojan Horses, Worms, Adware, Spyware - when standard anti-virus software either fails to detect them or fails to effectively eliminate them. Standard antivirus programs are good at detecting this Malware, but not always good at effectively removing it. Trojan Remover is designed specifically to disable/remove Malware without the user having to manually edit system files or the Registry. The program also removes the additional system modifications some Malware carries out which are ignored by standard security applications. Trojan Remover is designed to work on Windows 2000/XP/Vista/7/8. Homepage Changelog Download Page Download | (6.8.8 Build 2624) |
- 13:35 - Komentari (0) - Isprintaj - #
PrivaZer 2.32.0
|
PrivaZer is a privacy cleaner that scans your computer and provides you with a complete report of all computer and Internet traces that can be found on your PC. You can review the results in the detail and choose to securely erase them from your disk. The program performs a very thorough scan that not only includes the common traces like registry, Internet history, cookies etc., but also looks for potential traces in your free disk space sectors. PrivaZer can permanently wipe all traces using secure deletion methods and also reset you free disk sectors to zero to eliminate all traces from previous delete operations. The initial scan and cleaning process can be a little time consuming (20-30 mins), depending on the size of your disks and number of traces found.
|
- 13:30 - Komentari (0) - Isprintaj - #
AVG Anti-Virus 2015 15.0 Build 5941
|
Essential protection that won't get in your way! If you use your computer every day, you need protection that's always there, constantly keeping you safe. With AVG Anti-Virus, you get hassle-free protection against today's most sophisticated threats, online and offline. AVG Anti-Virus includes our unique LinkScanner® to prevent you from accidentally visiting harmful sites. It's faster, smarter security that won't slow you down. AVG Antivirus is one of the most complete programs we have found to date. It includes many new options to make it one of the most effective virus scanners on the market. It is still plagued by horrible slowdowns at times. Even things so simple as just typing an IM can be stopped for several seconds for some reason. If you can get passed the occasional slowdowns of your computer, the scanning functionality of AVG Antivirus is top of the line. With the rewrite of the scanning engine, AVG includes multi-processor support. Homepage Changelog Download | Anti-Virus (Online Installation) Download | Anti-Virus (Offline Installation - x86) Download | Anti-Virus (Offline Installation - x64) Download | Internet Security (Online Installation) Download | Internet Security (Offline Installation - x86) Download | Internet Security (Offline Installation - x64) Download | AV Free (Online Installation) Download | AV Free (Offline Installation - x86) Download | AV Free (Offline Installation - x64) |
- 13:14 - Komentari (0) - Isprintaj - #
18.05.2015., ponedjeljak
360 Total Security 6.8.0.6012 (All Windows versions)
|
360 Total Security - Provides comprehensive protection against the latest security threats with a triple virus detection engine and so much more. Features: Checkup Fast checking the overall condition of your computer's safety and healthy in one click. Virus Scan Integrated five top award antivirus engines including 360 Cloud Engine / QVMII / Avira and Bitdefender to offer you complete protection and best detection. Speedup Manage and optimize boot-up applications / plug-ins and services. Shorten your PC boot time, let it get ready soon. Cleanup Helps you to save disk space, cleans junks from your computer and makes it run more efficiently. Protection Protect your computer away from malware / phishing / backdoor and new type of threats via fastest and more intelligent cloud technology. What's New (for Windows 10 only): v6.8.0.6012 (2015-05-13): Added: Support Windows 10 Technical Preview (Build 10074) v6.8.0.6009 (2015-04-03): Added: Support Windows 10 Technical Preview (Build 10041) v6.0.0.6002 (2015-01-27): Added: Support Windows 10 Technical Preview (Build 9926) Download | All Windows |
- 17:31 - Komentari (0) - Isprintaj - #
Tor Browser 4.5.1
|
Tor is a toolset for a wide range of organizations and people that want to improve their safety and security on the Internet. Using Tor can help you anonymize web browsing and publishing, instant messaging, IRC, SSH, and other applications that use the TCP protocol. Tor also provides a platform on which software developers can build new applications with built-in anonymity, safety, and privacy features. The Tor Browser Bundle lets you use Tor on Windows, Mac OS X, or Linux without needing to install any software. It can run off a USB flash drive, comes with a pre-configured web browser to protect your anonymity, and is self-contained. Download | 4.5.1 Download Page | All languages and packages |
- 16:28 - Komentari (0) - Isprintaj - #
Microsoft Security Essentials 4.8.204.0
|
Microsoft Security Essentials provides real-time protection for your home PC that guards against viruses, spyware, and other malicious software. Microsoft Security Essentials is a free download from Microsoft that is simple to install, easy to use, and always kept up to date so you can be assured your PC is protected by the latest technology. It's easy to tell if your PC is secure — when you're green, you're good. It's that simple. Microsoft Security Essentials runs quietly and efficiently in the background so that you are free to use your Windows-based PC the way you want—without interruptions or long computer wait times. Download Page | 4.5.1 Download Page | All Languages |
- 16:27 - Komentari (0) - Isprintaj - #
|
07/2015 (2) 06/2015 (15) 05/2015 (64) |
|
Visitors |